One of our clients recently bought a “Kobo Clara Colour” an affordable color e-book reader. She wanted a straightforward way to enjoy her books, especially recipes, without the hassle of needing a traditional tablet (hard to read, too bright, low battery life, etc). Then she encountered the annoying “create an account” hurdle that many e-reader owners encounter.
// Account Requirements: An Unnecessary Barrier
As soon as the tablet powers on, the operating system immediately demands a Wi-Fi connection and requires you to create an account or log into an existing one. While it’s not limited to the manufacturer’s account—and, to be fair, offers an unusually long list of sign-in options—this requirement still feels intrusive. Creating a throwaway account might seem like a workaround, but it doesn’t address the core issue: users shouldn’t be forced to register just to use a tablet for reading content.
Even a throwaway account poses risks, as it can expose personal data like your email to potential leaks, making you vulnerable to spam and phishing attempts. If any payment details or personal information are linked to the account, they could be at risk should the tablet end up in the wrong hands, allowing unauthorized access to sensitive data. Beyond that, even using a “dummy” account still creates a digital footprint, which could be exploited for data mining or other invasive practices by third parties.
A quick online search reveals that a new “side-load” mode was apparently added, though, unfortunately, it doesn’t seem to be available on our particular tablet.
// Investigating the Tablet’s Workarounds
Although the tablet is relatively inexpensive, damaging a client’s equipment is never acceptable. We obtained the same model and began investigating. What’s absurd is that, even without an account, if you do not connect it to the Wi-Fi, you can connect the tablet to a computer and access local storage to side-load e-books. This allowed us to explore the tablet’s internal configuration within the file directory.
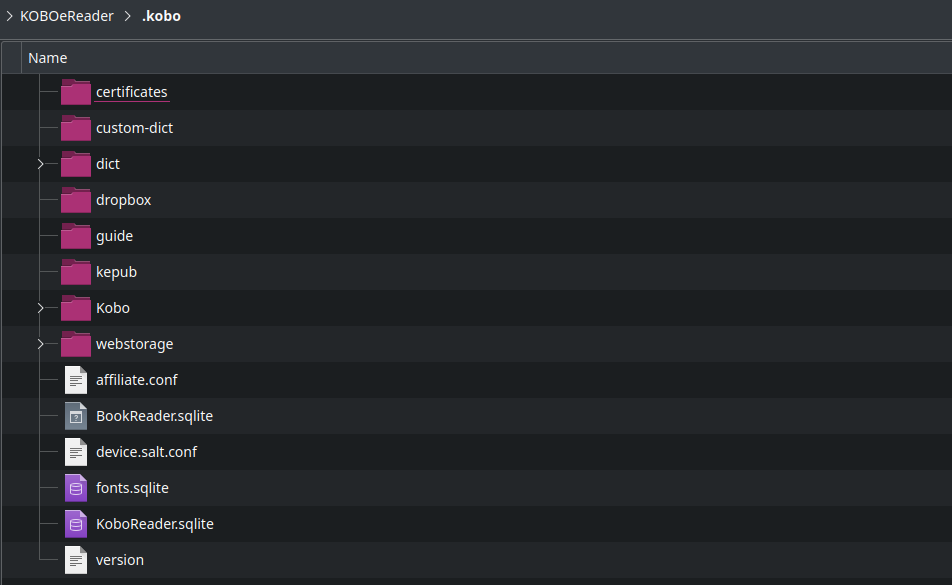
The user account data is stored in a hidden folder called “.kobo” so make sure you configure your file browser to display hidden folders. The database is called “KoboReader.sqlite”. This is a SQLite embedded database. To open it, you will need to download the SQLite toolkit.
After SQLite is installed, open terminal, make sure you are in the “.kobo” directory and run the command bellow to open the database.
sqlite3 KoboReader.sqliteOnce the database is opened, you can use the command to create an user in the database.
INSERT INTO user(UserID,UserKey) VALUES('1','');To exit SQLite, use the shortcut “CTRL+D”. Add your favorite e-book and safely eject the e-reader’s internal storage from your computer, then disconnect it. Restart the tablet, and you should be able to continue as if you already had an account, allowing you to enjoy your content fully offline.

// Hacking Your Tablet
Most of the tablet’s functionality, including the built-in web browser, should still work. You won’t be able to access online stores to buy books directly from the tablet, but for us, this is an advantage as it reduces the risk of credit card information being compromised. We recommend avoiding Wi-Fi connections and using a USB cable to side-load content instead. Although updates can address security issues, if the tablet is kept offline, this isn’t a concern. In fact, updating could potentially disable this workaround or even risk bricking the device. Please note that PDFs with DRM cannot be used for obvious reasons.
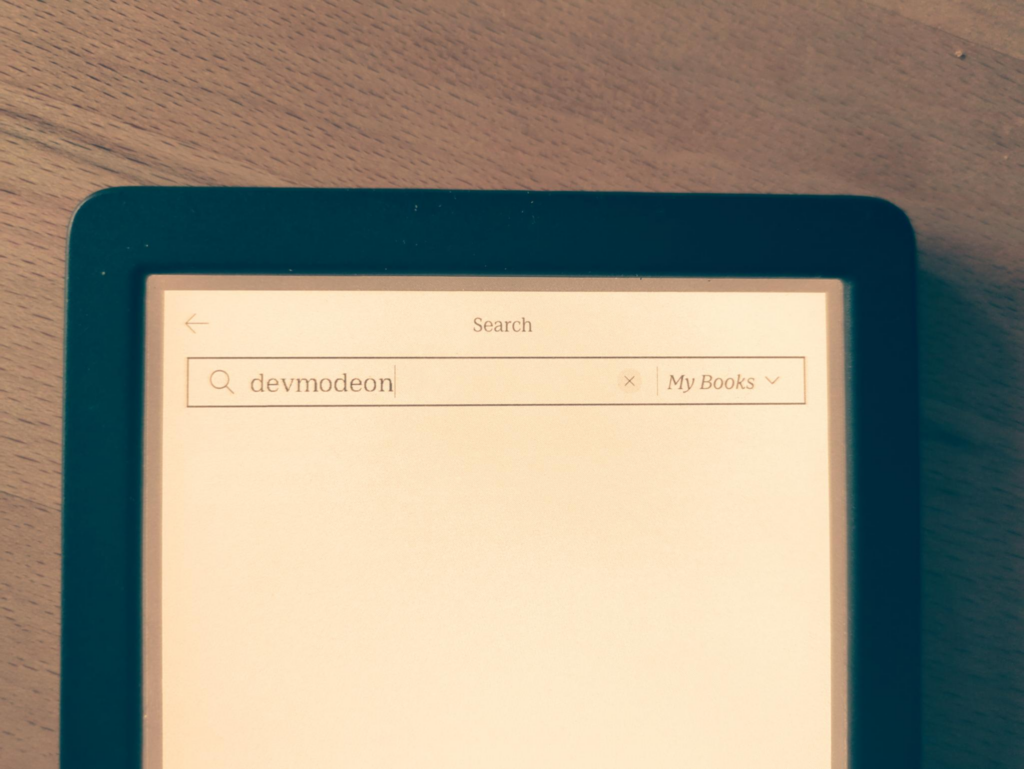
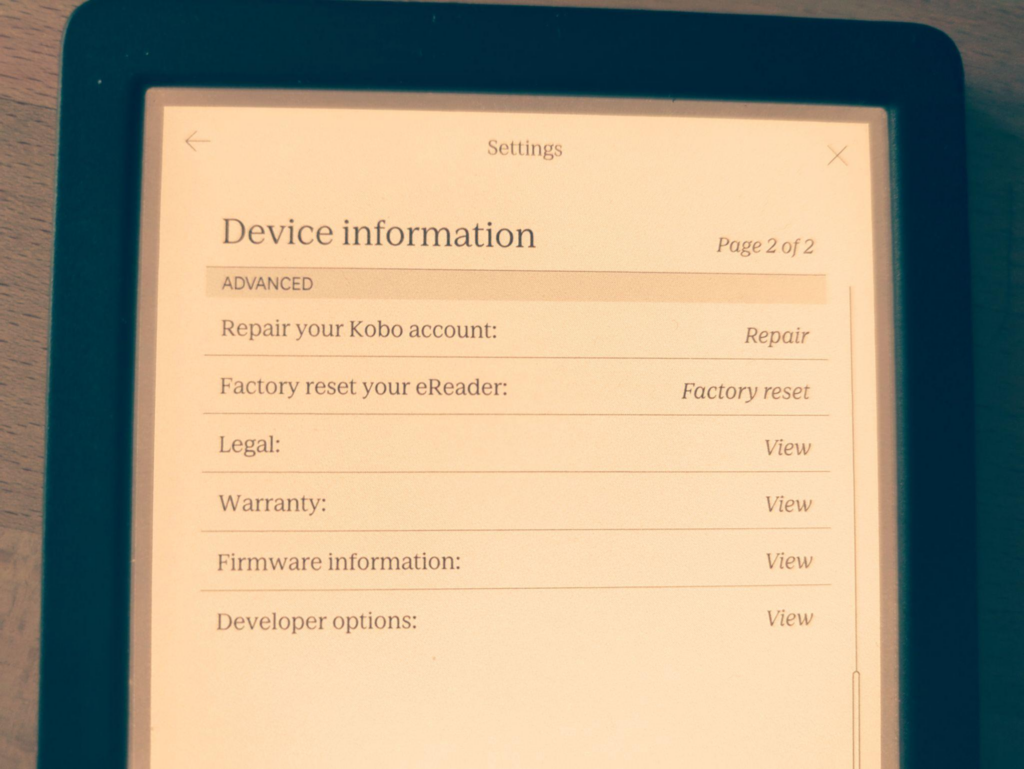
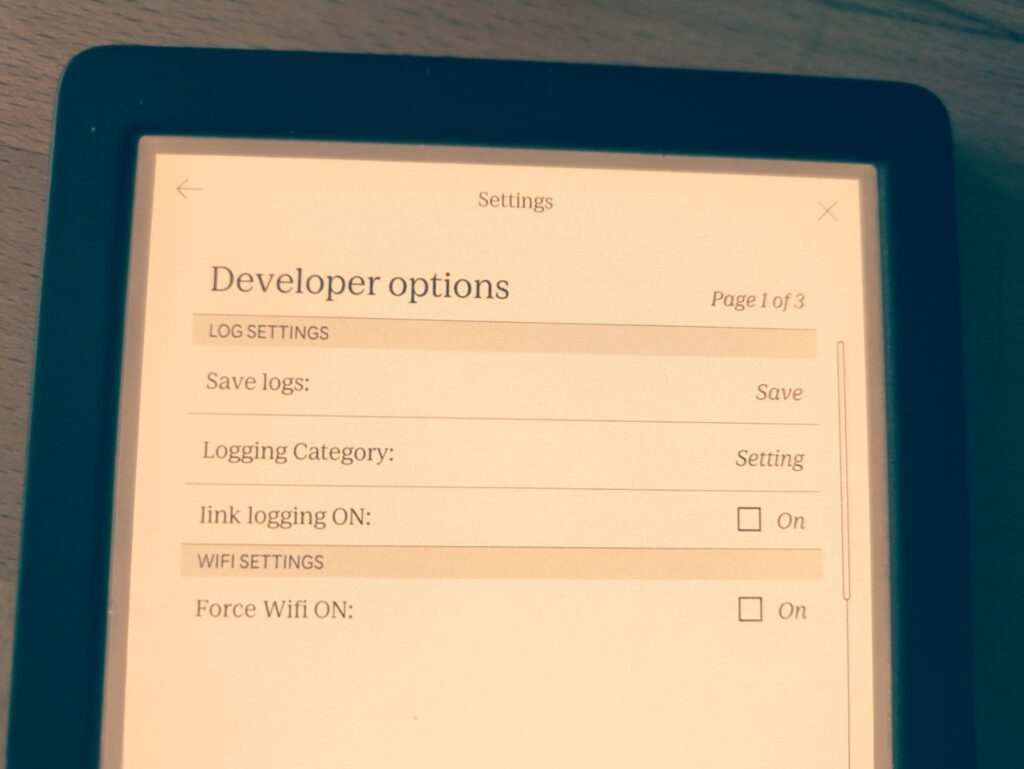
Here’s a hidden bonus: go to “My Books” and click on the search button, then type “devmodeon”. While it won’t return any results (unless you happen to have a book titled devmodeon), it will activate developer mode. You can then access the developer options under “More” -> “Settings” -> “Device Information” -> “Developer options”.
In a hyper-connected world, taking control of your device means reclaiming a bit of freedom. By keeping your tablet offline, side-loading content yourself, and even tapping into hidden developer options, you’re choosing privacy and security over the noise of updates, ads, and potential vulnerabilities. This is about using technology on your own terms, without outside influence.
Remember, the more you understand and manage your technology, the more it works for you—not the other way around.

Private Consulting
We offer one-on-one consulting for those who want to go beyond our default offerings. Few humans have the experience and knowledge we do with a private and self-sovereign living.



 We Accept // Bitcoin | Monero | Credit Card
We Accept // Bitcoin | Monero | Credit Card